No edit summary |
No edit summary |
(No difference)
| |
Latest revision as of 17:01, 15 October 2021
Introduction to the Problem
On September 30 2021 Let's Encrypt's DST Root CA X3 certificate expired, causing issues to most of the older devices and operating systems when connecting to websites and online services.
Let’s Encrypt is organisation that issues SSL certificates to encrypt connections between the web server and client (your device).
Millions of devices were affected, computers running on older operating systems, older devices like game consoles, smart phones and mobile devices and other devices. In same time many companies, websites and online services were facing and reporting issues.
For more information visit the official announcement on Let's Encrypt's website.
The founder of Security Headers, Scott Helme has been tracking the issue and explained:
There are a couple of ways to solve this depending on what the exact problem is, but it boils down to: The service/website needs to update the certificate chain they are serving to clients or, the client talking to the website/service needs an update.
For the affected companies, it's not like everything is down, but they're certainly having service issues and have incidents open with staff working to resolve. In many ways, I've been talking about this for over a year since it last happened, but it's a difficult problem to identify. It's like looking for something that could cause a fire: it's really obvious when you can see the smoke!
Long story short, the companies knew about it and yet they have not prevented those issues from happening on time.
Many companies posted announcements and notices on their website, informing their customers and users of the issue and providing them a temporary workaround for the issue until they come with a long term solution.
But not BigPoint and the "New Drakensang Team". We have been hearing crickets from their side ... as usual.
Fortunately this game is indeed , blessed with a great community, and the community members were exploring solutions and helping other players on their own!
Users don't have to manage their certificates on their own, those certificates are managed by administrators and programs that are using those certificates.
Affected DSO Users
Let us first see how is this issue affecting DSO and the players.
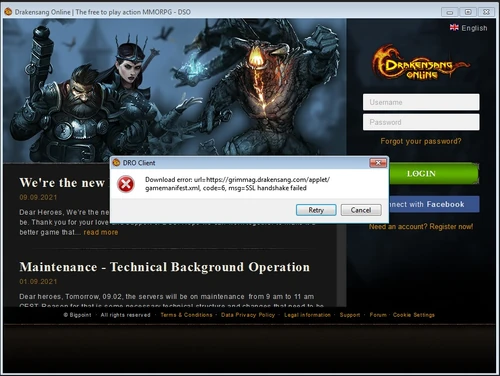
The client can't connect with the server, when launched.
Temporary Workarounds
However, the game could be played in browser with no issues (check on this guide on how to play the game in browser ). But since the game is running its 32bit version in a browser, version which has issues and crashes frequently, the players were asking for a way to play the game in the client.
One of the "workarounds" is suggesting setting the system time back to the time before the expiration of the certificate. This workaround is working but it is sort of illegal.
Therefore we need to come up with better solution.
There are some folks that are reporting issues with the game's website. They can't access it with browser.
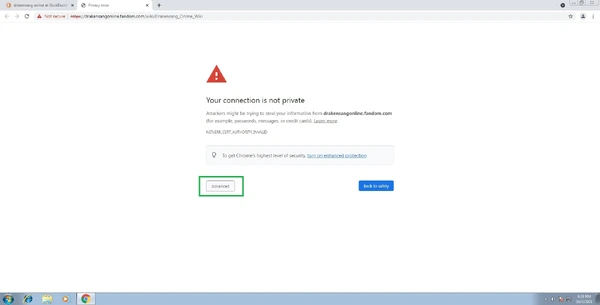
In example someone can't access using Google Chrome. The temporary solution is simple. When you get this "Privacy Error":
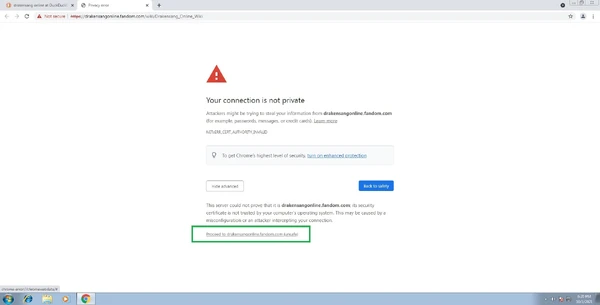
just click on "Advanced" button and them click the link which is marked as unsafe.
Or just click on the blank space and type "thisisunsafe" in order to prevent warnings and add the website on the safe list.
Personally, I had issues only a day or two and then the issue got resolved on its own or probably the protocols were updated by BP.
But there are people who are still having issues, thus making this guide.
Solution
First we need to download all the required files, 3 in total.
Needed Files
Download the files from these links:
Don't worry these links are official downloading links, they are safe and clean. ;)
Download them and save them somewhere for later use.
Registry Editing
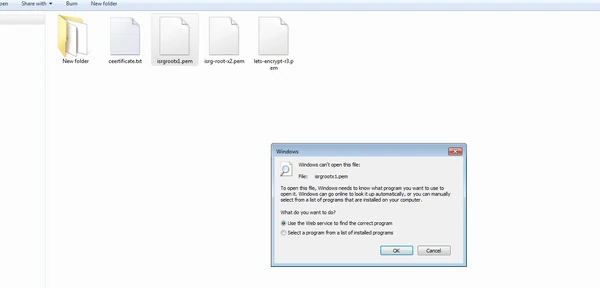
When downloaded, these files are probably going to be blank and not associated with any program.
We need to associate them with Crypto Shell Extensions.
In order to do that we will execute a simple script.
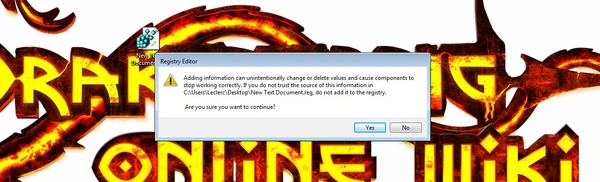
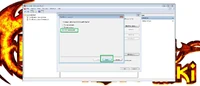
First, create a new blank text document and name it whatever you like. Then open the document and paste the following code:
Windows Registry Editor Version 5.00 [HKEY_CLASSES_ROOT\.pem] @="CERFile" "Content Type"="application/x-x509-ca-cert"
Save the changes and close the file. Then click on the file name and change the file extension from ".txt" to ".reg".
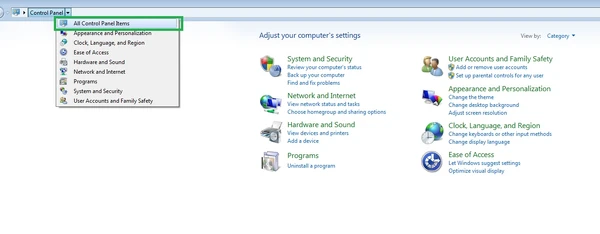
Note: If you can't see file extensions you will have to go to Control Panel -> Folder Options. If you can't see Folder Options you need to select "All Control Panel Items" from the drop down menu:
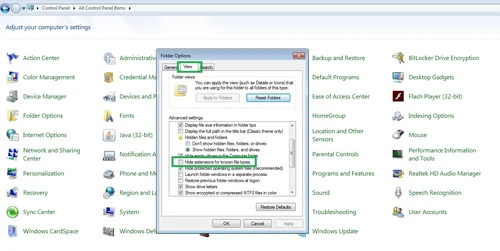
Open Folder Options, under "View" tab, untick "Hide extensions for known file types".
Press "Apply", then "OK".
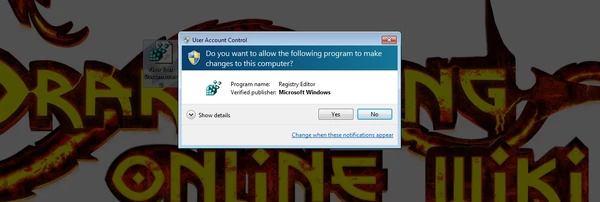
Now, when the file extension is changed to ".reg", double click on the file and then when prompted select "Yes" -> "Yes" -> "OK".
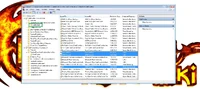
You need to restart your PC. After the restart you should be able to see the files associated with correct program and icons.
Installing Certificates
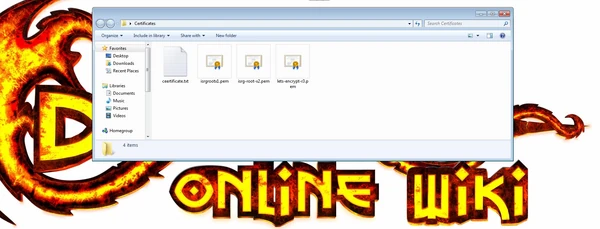
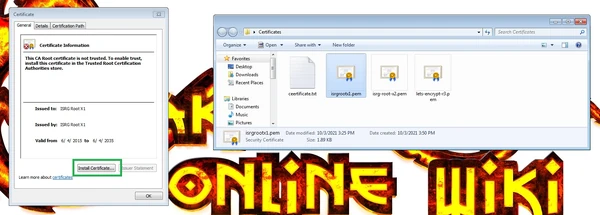
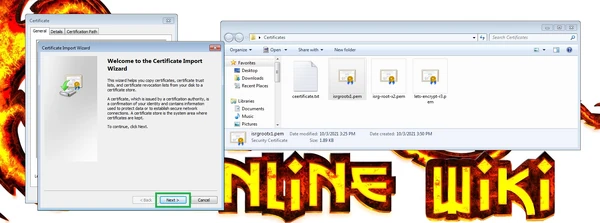
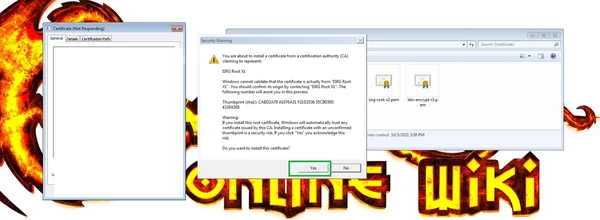
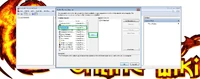
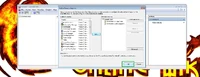
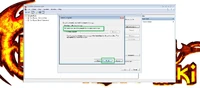
Open the folder with the files and double-click on any one file. Certificate Import Wizard will open. Select "Install Certificate".
Then select "Next".
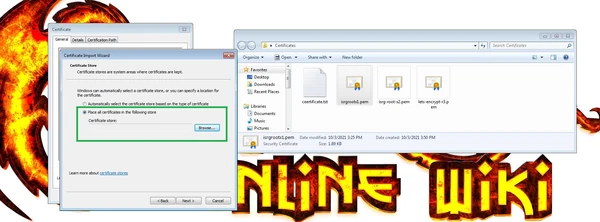
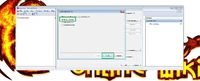
Then select "Place all certificates in the following store" and pes the "Browse" button.
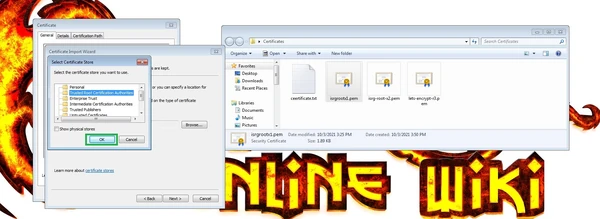
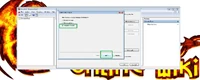
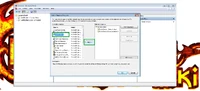
From the opened certificate store list, select "Trusted Root Certification Authorities"
Press "OK".
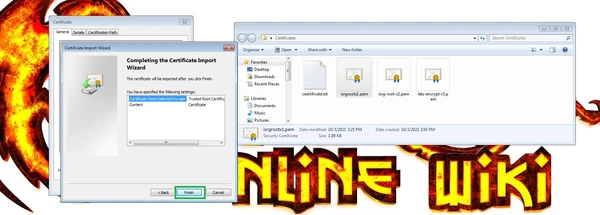
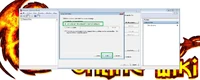
Then press "Finish".
If you get Security Warning, press "Yes".
You need to repeat all these steps for the other two files.
After finishing all the steps with all three files you have those certificates installed. Next you could add Snap-ins but it is not necessary step, it is completely optional. If you are not doing the optional part you can restart your computer and you are good to go.